Corley, Jacqueline S., United States Magistrate Judge
This document relates to: ALL ACTIONS
Counsel
Lesley E. Weaver (SBN 191305)BLEICHMAR FONTI & AULD LLP
555 12th Street, Suite 1600
Oakland, CA 94607
Tel.: (415) 445-4003
Fax: (415) 445-4020
lweaver@bfalaw.com
Derek W. Loeser (admitted pro hac vice)
KELLER ROHRBACK L.L.P.
1201 Third Avenue, Suite 3200
Seattle, WA 98101
Tel.: (206) 623-1900
Fax: (206) 623-3384
dloeser@kellerrohrback.com
Plaintiffs’ Co-Lead Counsel
Additional counsel listed on signature page
Orin Snyder (admitted pro hac vice)
GIBSON, DUNN & CRUTCHER LLP
200 Park Avenue
New York, NY 10166-0193
Tel: 212.351.4000
Fax: 212.351.4035
osnyder@gibsondunn.com
Counsel for Defendant Facebook, Inc.
Additional counsel listed on signature page
STIPULATION AND [PROPOSED] ORDER GOVERNING THE PRODUCTION OF ELECTRONICALLY STORED INFORMATION AND HARD COPY DOCUMENTS
A. PURPOSE
This Order will govern discovery of electronically stored information (“ESI”) and hard copy documents (collectively, “Document” or “Documents”) in the above-captioned matter and all actions that are later consolidated with this matter (collectively, “Litigation”), as a supplement to the Federal Rules of Civil Procedure, this Court’s Guidelines for the Discovery of Electronically Stored Information (“ESI Guidelines”), and any other applicable orders and rules.
Nothing in this Order establishes any agreement as to either the temporal or subject matter scope of discovery in the Litigation, or whether a party has made a reasonable and diligent search for Documents. Nothing in this Order establishes any agreement to any search protocol, including which sources shall be searched. Such procedures or criteria are to be separately agreed upon.
This Order is subject to amendment or supplementation based upon the results of anticipated future meet and confers and by later agreement of the parties, if necessary, in light of further developments, including, the parties’ engagement of document hosting vendors and associated technical requirements. References are made to the Federal Rules of Civil Procedure for ease of reference.
B. COOPERATION AND PROPORTIONALITY
The parties are aware of the importance this Court places on cooperation in discovery, consistent with this Court’s Guidelines for the Discovery of ESI. The parties acknowledge that cooperation in reasonably limiting ESI discovery requests and in reasonably responding to ESI discovery requests tends to reduce litigation costs and delay and commit to cooperation in good faith on issues relating to the preservation, collection, search, review, and production of ESI.
The parties acknowledge that the proportionality standard described in Guideline 1.03 and set forth in Fed. R. Civ. P. 26(b)(1) applies to the discovery of ESI in this action. To further the application of the proportionality standard, the parties agree that the factors set forth in Guideline 1.03 shall be considered, and that all discovery requests for production of ESI and related responses should and will be reasonably targeted, clear, and as specific as practicable.
C. E-DISCOVERY LIAISONS
The parties will rely on one or more e-discovery liaisons, as needed, to confer about ESI and to help resolve disputes without court intervention. Each e-discovery liaison will be, or have access to those who are:
- knowledgeable about the respective party’s e-discovery efforts;
- familiar with the respective party’s electronic systems and capabilities in order to explain those systems and answer relevant questions; and
- knowledgeable about the technical aspects of e-discovery, including the nature, location, storage, accessibility, format, collection, search methodologies, and production of ESI in this matter.
Plaintiffs have previously identified an ESI liaison. Defendant will identify an ESI liaison or liaisons within ten days of the entry of the order adopting of this Stipulation. In the interim, Defendant’s counsel will be prepared to discuss any ESI issues within a reasonable time after notice by Plaintiffs’ counsel. Each party will notify the other of any changes of its designated e-discovery liaison or liaisons.
D. PRESERVATION
The parties and their counsel acknowledge that they have an obligation to take reasonable and proportional steps to preserve discoverable information in the party’s possession, custody, or control consistent with the Federal Rules. In accordance with ESI Guideline 2.01(d), the parties will continue to meet and confer over their respective ESI preservation efforts and obligations. If the parties are unable to resolve a preservation issue and one party wishes to raise the issue with the Court, that party shall do so promptly, consistent with the Court’s order on Discovery Dispute Resolution Procedures (Dkt. No. 393).
The parties have discussed their preservation obligations and needs and agree that preservation of potentially relevant ESI will be reasonable, proportionate, and within the scope of production under FRCP 26(b)(1) and 26(b)(2)(B). To reduce the costs and burdens of preservation and to ensure discoverable ESI is preserved, the parties agree that:
(a) ESI created, modified, or received since January 1, 2007, will be preserved;
(b) Each party is responsible for taking reasonable and proportionate steps to preserve non duplicative discoverable information currently in their possession, custody or control. However, parties shall not be required to modify, on a going-forward basis, the procedures used by them in the usual course of business to back up and archive data not subject to a litigation hold.
(c) Subject to and without waiving any protection described above, the parties agree that:
(1) The parties will meet and confer regarding the types of ESI they believe should be preserved, the custodians or general job titles or descriptions of custodians for whom they believe ESI should be preserved, and the custodial and non-custodial sources to be preserved. Nothing in this Order waives or modifies the attorney–client-privilege that attaches to custodial interviews.
(2) The parties shall agree to add or remove custodians and non-custodial sources to be preserved as reasonably necessary. Such requests must be made in good faith. (3) The parties will meet and confer as fact discovery proceeds on whether an extension of time for fact discovery may be necessary.
(d) The parties agree that ESI from the following data sources is not reasonably accessible because of undue burden or cost and therefore that under Fed. 26(b)(2)(B) Facebook need not provide discovery of ESI from these sources (ESI from these sources will be preserved in accordance with Facebook’s standard business practices but will not be searched, reviewed, or produced unless ordered by the Court):
(1) backup systems and/or tapes used for disaster recovery; and
(2) systems that are no longer in use and cannot be accessed.
(e) The parties agree, based on mutual representation of the parties’ counsel, that the following sources of data are not reasonably accessible and need not be preserved, collected, processed, reviewed and/or produced:
(1) Deleted, slack, fragmented, or unallocated data generated on individual workstations, and only accessible by forensics;
(2) Random access memory (RAM), temporary files, or other ephemeral data generated on individual workstations and that are difficult to preserve without disabling the operating system;
(3) On-line data from the individual work stations of the employees of the producing party using internet browsers, such as temporary internet files, history, cache, cookies, and the like;
(4) Data in the following metadata fields, which are frequently updated automatically without end user intervention: last opened dates and times, last printed dates and times, last modified dates and times, and last modified by; and
(5) Information created or copied during the routine, good-faith performance of processes for the deployment, maintenance, retirement, and/or disposition of computer equipment by the party and belonging to a custodian, to the extent such information is duplicative of information that resides in a reasonably accessible data source.
(f) The parties agree that the burden and expense of preservation of the following sources of data for all agreed custodians is not proportionate to the needs of the case and therefore agree (i) to conduct custodial interviews and to determine in those interviews whether any of the following sources is likely to contain relevant data from that custodian; (ii) that if a custodian identifies any of the following sources as likely containing relevant data, that source will be preserved and collected; and (iii) that if a custodian does not identify any of the following sources as likely containing relevant data, these sources will not be preserved or collected:
(1) Voicemails and other voice messages;
(2) Sound recordings, including without limitation .mp3 and .wav files;
(3) Information contained on a mobile device that is not duplicative of information that resides in an another, more easily accessible data source;
(4) Instant messages and chats that are not chronicled to an email archive system; and
(5) Mobile device activity logs for the Producing Party’s devices or the Producing Party’s employees’ devices.
E. SEARCH AND REVIEW
The parties agree to meet and confer concerning search methodologies, including without limitation, the use of keyword search terms and/or the use of technology assisted review (“TAR”)[1]. The parties recognize that even though a document contains one or more of the search terms identified in accordance with the procedures listed below, such document may not be responsive to any document request. In such cases, the Producing Party is not required to produce such documents. If a document contains one or more of the search terms in accordance with the procedures listed below, and part but not all of the document is responsive to any document request, the Producing Party should produce the entire document without redacting the nonresponsive portions of the document, unless the nonresponsive portions of the document contain information (1) that would be redacted from a court filing under Fed. R. Civ. P. 5.2(a) or (2) the disclosure of which would threaten serious competitive harm to the Producing Party. If either of those conditions is met, the parties will meet and confer to discuss the redaction of such information prior to the production of any redacted documents. If the parties reach agreement regarding the redaction of such information and any portion of a document is subsequently produced in redacted form, this will be noted in the Redaction field, included in Table 1 of Appendix A, and, within 20 days of the production of such documents, the document(s) will be recorded on a cumulative log identifying the reason for the redaction (i.e. condition (1) or condition (2)) and the date upon which the parties reached agreement regarding the redaction. If the parties are unable to reach agreement regarding redaction, the document should either be promptly produced without redaction, or the Producing Party shall promptly raise the issue with the Court, consistent with the Court’s order on Discovery Dispute Resolution Procedures (Dkt. No. 393). In addition to identifying documents pursuant to an agreed upon search protocol, the parties recognize that they are obligated to produce relevant, responsive, non-privileged documents of which they are aware, regardless of whether such documents contain any of the agreed upon or additional search terms.
The parties agree that in responding to an initial Fed. R. Civ. P. 34 request, or earlier if appropriate, they will meet and confer about methods to search ESI in order to identify ESI that is subject to production in discovery and filter out ESI that is not subject to discovery. The parties understand the cost and complexity of reviewing and producing ESI and seek to engage in a cooperative, iterative process to limit costs but ensure relevant, responsive documents are likely discovered in any ESI search. As such, the parties will cooperate regarding the disclosure and formulation of appropriate search terms for use in the responsiveness review and production of ESI. The parties are not required to exchange privileged search terms.
The parties will each disclose a list of the most likely custodians of relevant documents, including the general job titles or descriptions of each custodian and will meet and confer regarding custodians, including how the relevant ESI is maintained and where, consistent with Discovery Order No. 1 (Dkt. No.404) and any subsequent orders entered by the Court.
The parties will meet-and-confer in good faith regarding search terms and custodians. As part of the meet-and-confer process to select search terms and custodians, the Producing Party will provide a hit report for proposed search terms if requested by the Requesting Party. If the Requesting Party objects to the sufficiency of the Producing Party’s proposed search terms, the Requesting Party may propose modifications to the Producing Party’s terms, or a list of additional terms, subject to the paragraph regarding Additional Terms for Good Cause below. Any disputes over additional custodians or terms that cannot be resolved between the parties during meet and confer may be presented to the Court.
Disputed Search Terms: If the Producing Party contends that terms proposed by the Requesting Party would recall an excessive number of documents (“Disputed Search Terms”), the Producing Party will provide a Disputed Search Term hit list or hit report after global de-duplication.
The list or report should include the number of documents that hit on each term, the number of unique documents that hit on each Disputed Term (documents that hit on a particular term and no other term on the list), and the total number of documents that would be returned by using the proposed search term list (including families). With respect to any search term for which the Producing Party believes there exists a modification that will reduce the number of irrelevant documents returned by the search term, the Producing Party will meet and confer with the Requesting Party to discuss in good faith any such modification. For any terms that a Producing Party believes are burdensome, overly broad, and/or objectionable and for which there does not appear to be any modification that would resolve such issues, the Producing Party will meet and confer with the Requesting Party to discuss in good faith its objections to such search terms. As part of that process, the Producing Party will, upon request, provide the Requesting Party with the quantitative information discussed above. In the event that a dispute remains after quantitative information is evaluated, the Requesting Party may ask for (and the Producing Party will not unreasonably withhold) qualitative information about the disputed search term(s). The Producing Party agrees to consider a reasonable number of good faith requests from the Requesting Party to review a random sample of documents and their family members with unique hits that hit on the disputed search terms and to discuss the results of that review with the Requesting Party. For any random sample that is reviewed, the parties will, in good faith, attempt to reach agreement on the appropriate sample size.
Additional Terms for Good Cause: Once a search term list is finalized (either though agreement of the parties or Order of the Court) and all iterative searches for a custodian are complete, the Requesting Party may propose additional search terms for a Producing Party to consider, but the Producing Party will have no obligation to re-search the custodian’s electronic data using such additional search terms without agreement or a court order. The Requesting Party must show good cause for any additional proposed search terms, such as, for example, that the proposed term, or the significance of the proposed term, was unknown to them as of the time the original list was formulated; provided, however, that this provision does not relieve a Producing Party of any obligation that may arise, pursuant to the Federal Rules of Civil Procedure or applicable case law, to conduct additional searches in the course of the litigation. If a Producing Party cannot meet any applicable deadlines for the production of documents as a result of this provision, the parties will negotiate in good faith a reasonable timeline for production or seek an order from the Court.
Known Responsive ESI: ESI that is known to a party to be responsive to a discovery request or subject to disclosure under Fed. R. Civ. P. 26(a)(1)A) may not be withheld on the grounds that it was not identified as responsive by the protocol described in, or developed in accordance with, this Order.
Discrete folders or collections of Documents that are identified by a custodian as likely to be responsive will be collected and preserved pursuant to standard business practices and processes that are reasonably designed to ensure all potentially responsive documents are identified and collected. The parties will continue to meet and confer regarding any search process issues as necessary and appropriate. This ESI protocol does not address or resolve any other objection to the scope of the parties’ respective discovery requests.
Nothing in this Order shall be construed or interpreted as precluding a producing party from performing a responsiveness review to determine if documents captured by search terms are in fact relevant to the requesting party’s request. Further, nothing in this Order shall be construed or interpreted as requiring the production of all documents captured by any search term if that document is in good faith and reasonably deemed not relevant to the requesting party’s request or is privileged.
F. PRODUCTION FORMATS
Appendix A sets forth the technical specifications that the parties propose to govern the form of production of documents in this litigation, absent agreement by the parties or order by the Court. The parties have agreed to specifications identifying the file formats under which Documents will be produced, as described in Appendix A. To the extent a party believes that a Document that has been produced should be produced in a different or alternative format, or a party raises any questions or concerns regarding a produced Document, the parties will meet and confer on the issue. ESI will be deduplicated globally across all custodians using industry standard deduplication methods and software as set forth in Appendix A.
Each party will use its best efforts to filter out common system files and application executable files by using a commercially reasonably hash identification process. Hash values that may be filtered out during this process are located in the National Software Reference Library (“NSRL”) NIST hash set list. System and program files defined on the NIST list need not be processed, reviewed, or produced. The parties may suppress container files (.ZIP, .PST, .RAR) that do not reflect substantive information prior to production, but must produce the remainder of those responsive, non-privileged document families found within the container file, including any emails to which that container file is attached. Similarly, the parties may suppress any non-substantive images extracted from email documents (e.g., logs, icons) prior to production).
E-mail thread analysis may be used to reduce the volume of emails reviewed and produced, provided the Producing Party discloses that it is using e-mail thread analysis. “E-mail thread analysis” means that where multiple email messages are part of a single chain or “thread,” a party is only required to produce the most inclusive message (“Last In Time E-Mail”) and need not separately produce earlier, less inclusive e-mail messages or “thread members” that are fully contained within the Last In Time E-mail. An earlier e-mail is fully contained in the Last In Time E-mail only if the Last In Time E-mail includes all previous emails, including attachments and identical senders and recipients, on the thread. Only email messages for which the parent document and all attachments are contained in the Last In Time Email will be considered less inclusive email messages. For avoidance of doubt, if a thread member contains any additional data that is not contained in the Last In Time E-mail (including without limitation attachments or BCC recipients), it is not a less-inclusive e-mail and must be separately produced. Where a Last In Time E-Mail is produced, the producing party will include metadata corresponding to the following metadata fields for each of the earlier thread members fully contained within the Last In Time E-mail: Sent Date, Sender, Recipient, CC, BCC, and Subject.
If a receiving party raises an issue regarding the usability or format of a produced Document, the parties the parties will meet and confer regarding whether an alternative form of production is necessary or appropriate and seek Court intervention only if necessary.
The parties recognize that certain information to be produced in discovery may reside in proprietary systems and formats. The producing party will take reasonable steps to produce documents from such sources in a reasonably usable format with appropriate metadata in line with how the information is kept in the usual course of business. If after reviewing the produced Documents a receiving party raises a specific issue or concern about a produced Document or data, the parties will meet and confer regarding whether an alternative form of production or additional metadata is necessary or appropriate.
G. DOCUMENTS PROTECTED FROM DISCOVERY
The provisions and protections of a Fed. R. Evid. 502 stipulation are being separately negotiated. The parties will submit a proposed 502(d) stipulation in accordance with the Court’s order (Dkt. No. 404).
H. PRIVILEGE LOGS
Where a document is withheld from production entirely or in part by redaction on the basis of the attorney-client privilege or work product doctrine, the Producing Party will produce a privilege log in Microsoft Excel format. The parties will meet and confer to determine a separate protocol for the production of privilege logs.
Nothing in this Order shall be interpreted to require disclosure of irrelevant information or relevant information protected by the attorney-client privilege, the work-product doctrine, or any other applicable privilege or immunity. The parties do not waive any objections to the production, discoverability, admissibility, or confidentiality of documents and ESI.
I. OBJECTIONS PRESERVED
Except as provided expressly herein, the parties do not waive any objections as to the production, discoverability, authenticity, admissibility, or confidentiality of Documents. Nothing in this Order waives the right of any party to petition the Court for an order modifying its terms upon sufficient demonstration that compliance with such terms is unreasonably burdensome or infeasible or that the production of particular Documents in a different format or with different metadata fields is reasonably necessary, provided, however that counsel for such party must first meet and confer with the counsel for the opposing parties and the parties shall use reasonable best efforts to negotiate an exception from or modification to this Order prior to seeking relief from the Court.
J. RETENTION OF ORIGINAL DOCUMENTS
Each party agrees to retain native electronic source documents for all ESI produced in this litigation unless another manner is mutually agreed upon by the parties. Each party agrees to use reasonable measures to maintain the original native source documents in a manner so as to preserve the metadata associated with these electronic materials at the time of collection.
K. MODIFICATIONS
This Stipulated Order may be modified by agreement of the parties memorialized in a Stipulated Order of the parties or by the Court.
L. TIMING AND PHASING OF PRODUCTIONS
When a party propounds discovery requests pursuant to Fed. R. Civ. P. 34, the parties agree to phase the production of ESI by producing documents on a rolling basis. Following the initial production, the parties will continue to meet and confer to prioritize the order of subsequent productions. Production in the Litigation is anticipated to be conducted with the parties making reasonable efforts to expedite the process.
M. EFFECTIVE DATE
The provisions of this ESI Protocol will take effect upon the entry of an order of the Court approving and adopting this ESI Protocol.
IT IS SO STIPULATED, THROUGH COUNSEL OF RECORD.
Dated: April 27, 2020
Respectfully submitted,
KELLER ROHRBACK L.L.P.
By: /s/ Derek W. Loeser
Derek W. Loeser
Derek W. Loeser (admitted pro hac vice)
Lynn Lincoln Sarko (admitted pro hac vice)
Gretchen Freeman Cappio (admitted pro hac vice)
Cari Campen Laufenberg (admitted pro hac vice)
David Ko (admitted pro hac vice)
Adele A. Daniel (admitted pro hac vice)
1201 Third Avenue, Suite 3200
Seattle, WA 98101
Tel.: (206) 623-1900
Fax: (206) 623-3384
dloeser@kellerrohrback.com
lsarko@kellerrohrback.com
gcappio@kellerrohrback.com
claufenberg@kellerrohrback.com
dko@kellerrohrback.com
adaniel@kellerrohrback.com
Christopher Springer (SBN 291180)
801 Garden Street, Suite 301
Santa Barbara, CA 93101
Tel.: (805) 456-1496
Fax: (805) 456-1497
cspringer@kellerrohrback.com
BLEICHMAR FONTI & AULD LLP
By: /s/ Lesley E. Weaver
Lesley E. Weaver
Lesley E. Weaver (SBN 191305)
Anne K. Davis (SBN 267909)
Joshua D. Samra (SBN 313050)
Matthew P. Montgomery (SBN 180196)
Angelica M. Ornelas (SBN 285929)
555 12th Street, Suite 1600
Oakland, CA 94607
Tel.: (415) 445-4003
Fax: (415) 445-4020
lweaver@bfalaw.com
adavis@bfalaw.com
jsamra@bfalaw.com
mmontgomery@bfalaw.com
aornelas@bfalaw.com
Plaintiffs’ Co-Lead Counsel
GIBSON, DUNN, & CRUTCHER LLP
By: /s/ Orin Snyder
Orin Snyder (pro hac vice)
osnyder@gibsondunn.com
200 Park Avenue
New York, NY 10166-0193
Telephone: 212.351.4000
Facsimile: 212.351.4035
Deborah Stein (SBN 224570)
dstein@gibsondunn.com
333 South Grand Avenue
Los Angeles, CA 90071-3197
Telephone: 213.229.7000
Facsimile: 213.229.7520
Joshua S. Lipshutz (SBN 242557)
jlipshutz@gibsondunn.com
1050 Connecticut Avenue, N.W.
Washington, DC 20036-5306
Telephone: 202.955.8500
Facsimile: 202.467.0539
Kristin A. Linsley (SBN 154148)
klinsley@gibsondunn.com
Martie Kutscher (SBN 302650)
mkutscherclark@gibsondunn.com
555 Mission Street, Suite 3000
San Francisco, CA 94105-0921
Telephone: 415.393.8200
Facsimile: 415.393.8306
Russell H. Falconer (pro hac vice pending)
2001 Ross Avenue, Suite 2100
Dallas, TX 75201
Telephone: 214.698.3170
Facsimile: 214.571.2900
Attorneys for Defendant Facebook, Inc.
IT IS SO ORDERED.
Dated: April 30, 2020
The Honorable Jacqueline Scott Corley
United States Magistrate Judge
APPENDIX A
I Production Format
All ESI is to be produced in an imaged file format with the corresponding metadata, appropriate load files, searchable text, and, where specified, native format files. The parties agree that certain file types should be produced in their native file format. Where ESI exists in databases or as structured data, production in an alternative format may be preferred and the parties agree to meet and confer to determine an appropriate format. To the extent that any party made a document production before the entry of this ESI protocol that included ESI that was produced in a format that differs from the agreed upon format described below, the parties agree that, where feasible, that ESI will be reproduced in the agreed-upon format described below. Where reproduction in that format is not feasible, the parties will meet and confer regarding a feasible production format.
A. TIFF Image Files. The parties agree that all Documents will be produced as single page, 1-BIT, black and white Group, IV TIFF image files of at least 300 dpi resolution, except as provided in section I.C. Page size shall be 8.5 x 11 inches unless otherwise agreed. Each image file will use the Bates number of the page as its unique file name. Bates numbers and confidentiality designations shall be branded on each produced image. Original document orientation as displayed in the native file should be maintained in the produced image (i.e., portrait to portrait and landscape to landscape). Where feasible, documents which contain hidden content, tracked changes, comments, deletions, or revision marks (including, where available, the identity of the person making the comment, deletion, or revision and the date and time thereof), speaker notes, or other user-entered data that the source application can display to the user shall be processed such that all such data is visible (or marked as redacted for privilege or pursuant to the procedure described in Section E of the ESI Protocol) in the produced image.
Where the TIFF image is unreadable or has materially degraded the quality of the original, or where the Requesting Party obtains through discovery a file or Document that it believes is not adequately represented in an image file format, the Producing Party will, upon reasonable request, re-produce the image in another feasible format (such as a reimaged TIFF, near-native reproduction, native format, or other reasonably usable format).
B. Text Files. Each Document produced under this Order shall be accompanied by a single, multipage text file containing all of the text for that item, not one text file per page. Each text file shall be named to use the Bates number of the first page of the corresponding production item.
1. OCR: The text for each hard copy document shall be generated by applying optical character recognition (“OCR”) technology to the scanned image of the document. The parties will endeavor to generate accurate OCR and will utilize quality OCR processes and technology. OCR text files should indicate page breaks where possible.
2. Text Files: The text of each ESI item shall be extracted directly from the ESI native file unless technologically infeasible. Extracted text shall include available comments, revisions, tracked changes, speaker notes, and hidden content (including, worksheets, slides, columns, rows, notes). To the extent it is not technically feasible to extract text directly from the native file the text for each ESI item shall be generated by applying OCR to the native file under the provision above. Text files will not contain the redacted portions of documents.
3. Foreign Language Text: In the event that discoverable ESI includes foreign language text and is produced in a way that it is otherwise unusable, the receiving party will raise the issue and the parties will meet and confer regarding an appropriate manner to reproduce the materials in a usable format.
C. Production of ESI in Native Format. The parties agree that the following types of files will be produced in native format: presentation-application files (e.g. MS PowerPoint); spreadsheet-application files (e.g., MS Excel, Google Sheets); and multimedia audio/visual files such as voice and video recordings, if any (e.g., wav, .mpeg, and .avi). Media files shall be produced in the native format in which they are maintained unless the parties discuss and agree to an alternative format in advance.
The Producing Party shall produce a single-page TIFF slip-sheet for each native file, indicating that a native item was produced. The corresponding load file shall include NativeLink information for each native file that is produced. If a Document to be produced in native format contains privileged or information redacted pursuant to the procedure set forth in Section E, the Document will be produced in TIFF format with redactions and OCR text to remove the privileged material from the searchable text.
D. Bates Numbering. Each TIFF image produced under this Order must be assigned a unique Bates number that must always: be unique across the entire Document production; maintain a constant length of the numeric digits (including 0-padding) across the entire production; contain only alphanumeric characters, no special characters or embedded spaces; and be sequential within a given Document.
Attachments to Documents and embedded objects extracted from or attached to Documents or e-mails will be assigned Bates numbers that directly follow the Bates numbers on the Documents to which they are attached. Parent-child relationships for all groups of hard copy documents as specified in section III.C.5, and all embedded ESI as specified in section I.F, will be indicated by applying sequential Bates numbers to all items within the parent-child group, and identified by Bates numbers in the relevant ESI metadata fields specified in section II. For example, if a party is producing an e-mail with attachments, the attachments will be processed and assigned Bates numbers in sequential order, following consecutively behind the parent e mail.
Each TIFF image will have its assigned Bates number electronically “burned” onto the image. The Producing Party will brand all TIFF images in the lower right-hand corner with its corresponding Bates number. If the placement in the lower right-hand corner will result in obscuring the underlying image, the Producing Party will attempt to adjust the Bates number as near to that position as possible while preserving the underlying image. If a Bates number or set of Bates numbers is skipped, the skipped numbers or set of numbers will be noted.
E. Attachments. The parties agree that if any part of an e-mail or its attachments is responsive, the entire e-mail and attachments will be considered responsive. The parties acknowledge that if any part of an e-mail or its attachments is privileged, that email and/or attachment may be withheld or redacted for privilege.
F. Embedded Files. The parties agree to take reasonable steps to ensure that embedded ESI (e.g., a spreadsheet embedded within a word processing document, multimedia and other word processing files embedded in PowerPoint) shall be produced as independent document records and that the parent-child relationship is indicated by assigning sequential Bates numbers as set forth in section D.
G. Color. The parties may submit reasonable requests for reproduction of documents in color where color is necessary to accurately interpret the document. The production of such Documents in color shall be made in JPEG format. If either party deems the quality of the Document produced in JPEG format to be insufficient, the Producing Party may produce the color image in TIFF or another reasonably usable format. All requirements for productions stated in this Order regarding production in TIFF black and white format apply to any production of Documents in color JPEG or TIFF format.
H. Confidentiality Designations. If a particular Document has a confidentiality designation, the designation shall be stamped on the face of all TIFF images pertaining to such Document, in the lower left-hand corner of the Document. Each responsive document produced in native format will have its confidentiality designation indicated on its corresponding TIFF placeholder. The confidentiality designation should also be reflected in the Confidentiality metadata field specified in section II.
I. Redaction. The parties agree that where non-Excel-type spreadsheet ESI items need to be redacted, they shall be produced solely in TIFF with each redaction clearly indicated on the Document. Any unaffected data fields specified in section II shall be provided.
The text file corresponding to a redacted Document may be generated by applying OCR in accordance with section I.B for all unredacted portions of the Document. The Document must be marked as such in the accompanying redaction metadata field as specified in section II. Documents redacted or withheld for privilege will be logged.
Where Excel-type spreadsheets need to be redacted, the Producing Party may choose whether to redact in the native file or in a TIFF format so long as such redactions do not affect the operation of the file. Formulas may be “flattened” and replaced with actual value. The party shall maintain the original Excel-type spreadsheet before redactions are applied as to maintain the original metadata fields.
If the items redacted and partially withheld from production are PowerPoint type presentation decks or Excel-type spreadsheets, and the native items are also withheld, the entire ESI item will be produced in TIFF format and the Producing Party will make reasonable efforts to produce all unprivileged pages, hidden fields and other information that does not print when opened as last saved by the custodian or end-user. For PowerPoint-type presentation decks, this shall include, but is not limited to, any speaker notes. For Excel-type spreadsheets, this shall include, but is not limited to, hidden rows and columns, all cell values, annotations and notes. The Producing Party shall also make reasonable efforts to ensure that any spreadsheets produced only as TIFF images are formatted so as to be legible. For example, column widths should be formatted so that the numbers in the column will display rather than “##########.” If the items redacted and partially withheld from production are audio/visual files, the Producing Party shall provide the unprivileged portions of the content. If the content is a voice recording, the parties shall meet and confer to discuss the appropriate manner for the Producing Party to produce the unprivileged portion of the content.
J. Encryption. To the extent practicable, before the application of search terms to a database of Documents, the searching party shall use reasonable efforts to de-encrypt encrypted Documents in the database if otherwise, without de-encryption, the search terms will not pick up hits in the encrypted Documents.
The parties will make reasonable efforts to ensure that all encrypted or password protected Documents are successfully processed for review and production under the requirements of this Order, including all automated mechanisms presently offered by the party’s document vendor and approaching the custodian for any relevant passwords, if the custodian is accessible, and if produced in Native format, the decrypted Document is produced. To the extent encrypted or password-protected Documents are successfully processed according to the requirements of this Order, the parties have no duty to identify the prior encrypted status of such Documents but will produce such processed Documents in accordance with the specifications of this Order. The parties will consider reasonable requests for information regarding the number, custodians, and/or locations of encrypted documents that are not able to be de-encrypted using reasonable means.
K. Database Records and Structured Data. To the extent that any party requests information that is stored in a database, or database management system, or proprietary system, the Producing Party will identify the database and platform to the Requesting Party, and will meet and confer in good faith in an attempt to reach agreement on the data to be produced and the form of the production to ensure that any information produced is reasonably usable by the Requesting Party and that its production does not impose an undue burden on the Producing Party, by, for example, requiring development of reports and/or software code to extract the information. The Producing Party will provide information about the database reasonably necessary to facilitate that discussion.
To avoid doubt, information will be considered reasonably usable when produced in CSV format, tab-delimited text format, Microsoft Excel format, or Microsoft Access format. To the extent a party is constrained from producing responsive ESI because of a third party license or because software necessary to view the ESI is hardware-dependent, the parties shall meet and confer to reach an agreement on alternative methods to enable the Requesting Party to view the ESI.
L. Deduplication. The Producing Party need only produce a single copy of a particular ESI item, and may deduplicate ESI vertically by custodian, or horizontally (globally) across the population of records. The parties agree to the following:
1. Duplicates shall be identified by using industry standard MD5 or SHA-1 algorithms only to create and compare hash values for exact matches only. The resulting hash value for each item shall be reflected in the HASH field specified in section II.
2. Deduplication shall be performed only at the Document family level so that attachments are not de-duplicated against identical stand-alone versions of such Documents and vice versa, although each family member shall be hashed separately for purposes of populating the HASH field in section II.
3. An email that includes content in the BCC or other blind copy field should not be treated as a duplicate of an email that does not include content in those fields, even if all remaining content in the email is identical. Deduplication may be applied across the entire collection (i.e., global level), in which case the custodian, filepath, and filename metadata fields should list the primary custodian, filepath, and filename, as a source of the primary copy of the document, while deduplicated custodians will be listed in the Duplicate Custodian, Duplicate Filepath field and separated by semicolons if there are multiple values. In the event that the Producing Party becomes aware that Duplicate Custodian,
Duplicate Filepath metadata has become outdated due to rolling productions, the Producing Party will produce within a reasonable time an overlay file providing all of the custodians, and filepaths for the affected documents.
M. Metadata Fields and Processing. ESI items shall be processed in a manner that preserves the source native file and all metadata without modification, to the extent reasonably and technically possible, including their existing time, date and time-zone metadata consistent with the requirements provided in this Order. ESI items shall be produced with all of the metadata and coding fields set forth in section II.
1. Time Zone. ESI items shall be processed to reflect the date and time standardized to a single time zone for all productions by a party, that time zone shall be Pacific Standard Time (PST). The parties understand and acknowledge that such standardization affects only dynamic fields and metadata values and does not affect, among other things, dates and times that are hardcoded text within a file. Dates and times that are hard-coded text within a file (for example, in an e-mail thread, dates and times of earlier messages that were converted to body text when subsequently replied to or forwarded; and in any file type, dates and times that are typed as such by users) will be produced as part of the document text in accordance with the formats set forth in section I.
2. Hidden Content. ESI items shall be processed in a manner that preserves hidden columns or rows, hidden text or worksheets, speaker notes, tracked changes, comments, and other rich data (including, but not limited to strikethrough text, etc.) as displayed in the Document to the extent reasonably and technically possible.
3. Manual Population. The parties are not obligated to manually populate any of the fields in section II if such fields cannot be extracted from the native file or created using an automated process with the exception of the following fields, if available: (1) BegBates; (2) EndBates; (3) BegAttach; (4) EndAttach; (5) Custodian; (6) Redacted (Y/N); (7) Confidentiality; (8) HashValue[2]; (9) DeDuped_Custodian; (10) NativeFile; and (11) TextPath.
N. Hard Copy Documents.
1. Coding Fields: All coding information defined in section II as applicable to “Paper,” shall be produced in the data load file accompanying production of hard copy documents.
2. Unitization of Hard Copy Documents: The parties will make reasonable efforts to ensure that hard copy documents are logically unitized for production. The parties will make their best efforts to unitize parent-child groups correctly.
3. Identification: Where a document or a document group – such as folder, clipped bundle, or binder – has an identifiable and accessible identification spine, “Post-It Note” or any other label, the information on the label shall be scanned and produced as the first page of the document or grouping if doing so would be reasonable and proportional to the needs of the case.
O. Load Files: All productions will be provided with data load files and image load file as detailed in section III.B & III.C. Each party will designate its preferred load file format. The image load file must reference each TIFF file in the corresponding production, and the total number of TIFF files referenced in the load file must match the total number of image files in the production. The total number of Documents referenced in a production’s data load file should match the total number of designated Document breaks in the corresponding image load file for that production.
II Production Metadata Fields
Parties shall produce extracted metadata for all Documents and include the following fields to the extent available and subject to other limitations above, except that if the field contains privileged information, that privileged information may be redacted. If burden or technological difficulty is claimed by the Producing Party, it must be disclosed to the Requesting Party. Any redactions for privilege reasons shall be recorded on a privilege log. The parties reserve the right to request that additional metadata fields set forth or provided for certain specified electronic documents upon review of the other party’s production. The parties also reserve their respective rights to object to any such request.

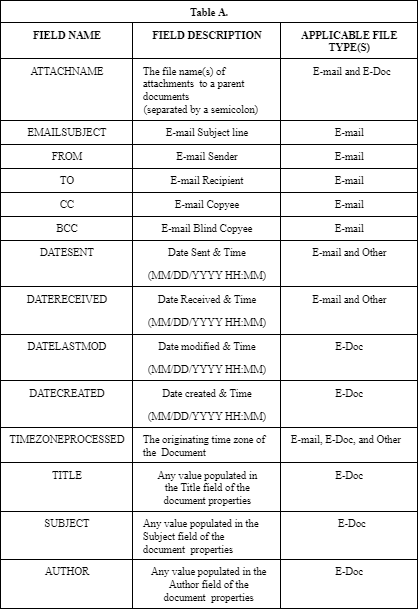
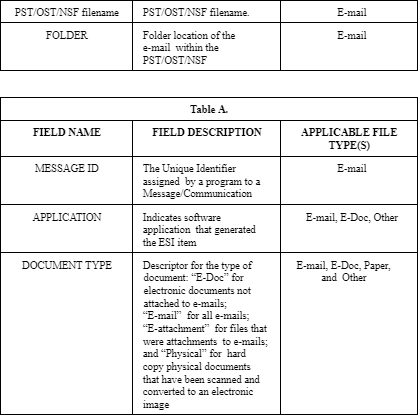
III Production Delivery Requirements
A. General Instructions
1. All productions must be made by secure file transfer, if practical, to agreed-upon e-mail addresses. In the event the Producing Party deems it is not practical to upload a voluminous production to secure file transfer site, it shall be sent to the receiving parties by overnight mail on CD-ROM, DVD, external hard drive (with standard PC-compatible interface), or such other readily accessible computer or electronic media.
2. Each production shall be accompanied by a cover letter that includes the production date, production volume identifier, confidentiality designation for the production, and the Bates number range.
3. Each media volume must have its own unique name and a consistent naming convention (for example ZZZ001 or SMITH001) and be labeled with the following:
a. Case number;
b. Production date;
c. Bates range;
d. Disk number (1 of X, 2 of X, etc.), if applicable.
4. The Producing Party shall encrypt the production data using WinRAR or 7-Zip (or similar AES-256 bit) encryption, and the Producing Party shall forward the password to decrypt the production data separately from the CD, DVD, external drive or FTP to which the production data is saved.
5. Any data produced by the Producing Party must be protected in transit, in use, and at rest by all in receipt of such data. Parties will use best efforts to avoid the unnecessary copying or transmittal of produced documents. Any copies made of produced data must be kept on media or hardware employing whole-disk or folder level encryption or otherwise secured on information systems and networks in a manner consistent with the best practices for data protection. If questions arise, Parties will meet and confer to ensure security concerns are addressed prior to the exchange of any documents.
B. Image Load Files
1. Image load (cross-reference) files should be produced in format that can be loaded into commercially acceptable production software, such as Concordance Image (Opticon) format.
2. The name of the image load file should mirror the name of the delivery volume, and should have the appropriate extension (e.g., ABC001.OPT).
3. The volume names should be consecutive (e.g., ABC001, ABC002, et seq.).
4. There should be one row in the load file for every TIFF image in the production.
5. Every image in the delivery volume should be cross-referenced in the image load file.
6. The imageID key should be named the same as the Bates number of the page.
7. Load files should not span across media (e.g., CDs, DVDs, hard drives, etc.), i.e., a separate volume should be created for each piece of media delivered.
8. Files that are the first page of a logical document should include a “Y” where appropriate. Subsequent pages of all documents (regular document, e-mail, or attachment) should include a blank in the appropriate position.
9. TIFF images should be provided in a separate folder and the numbe of TIFF files per folder should be limited to 1,000 files.
Sample Concordance Image (Opticon) Load File:
MSC000001,MSC001,D:\IMAGES\001\MSC000001.TIF,Y„,3
MSC000002,MSC001,D:\IMAGES\001\MSC000002.TIF,,,,,
MSC000003,MSC001,D:\IMAGES\001\MSC000003.TIF,,,,,
MSC000004,MSC001,D:\IMAGES\001\MSC000004.TIF,Y,,,2
MSC000005,MSC001,D:\IMAGES\001\MSC000005.TIF,,,,,
C. Data Load Files:
1. Data load files should be produced in .DAT format.
2. The data load file should use standard delimiters:
a) Comma - ¶ (ASCII 20);
b) Quote - þ (ASCII 254);
c) Newline - ® (ASCII174).
3. The first line of the .DAT file should contain the field names arranged in the same order as the data is arranged in subsequent lines.
4. All date fields should be produced in mm/dd/yyyy format.
5. All attachments should sequentially follow the parent document/e-mail.
6. Use carriage-return to indicate the start of the next record.
7. Load files should not span across media (e.g., CDs, DVDs, hard drives, etc.); a separate volume should be created for each piece of media delivered.
8. The name of the data load file should mirror the name of the delivery volume, and should have a .DAT extension (e.g., ABC001.DAT).
9. The volume names should be consecutive (e.g., ABC001, ABC002, et seq.).
10. Sample .DAT Load File:
þBegBatesþ¶þEndBatesþ¶þBegAttachþ¶þEndAttachþ¶þPgCountþ¶þCustodianþ
D. OCR/Extracted Text Files
1. OCR or Extracted Text files shall be provided in a \TEXT\ directory containing Document level text files.
2. Document level OCR text for redacted documents or Extracted text for ESI not containing redaction are to be located in the same directory as its image file.
3. The text file name shall be the same name of the first image page for the
document set, followed by .txt.
4. An OCR or Extracted text file containing the produced document’s content will
be provided for all documents whether it is produced as an image file or natively.
5. An OCR file may be provided for ESI when privilege redactions are required or
where extracted text isn’t otherwise available
E. Native Files
1. Native files shall be provided in a separate NATIVES\ directory containing the Native file referenced in the NativeFilePath field of the .DAT file.
2. The Native file name shall be the same name as the first image page for the document.